Getting started with HashiCorp Vault on Kubernetes
Exploring how to install and use Vault on Kubernetes...
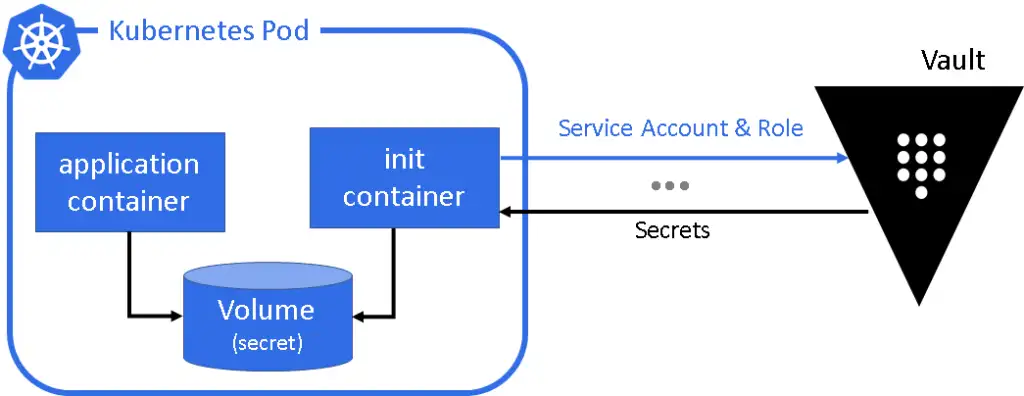
Actually using Vault on Kubernetes
In the previous article we configured Vault with Consul on our cluster, now it's time to go ahead and use it to provision secrets to our pods/applications...
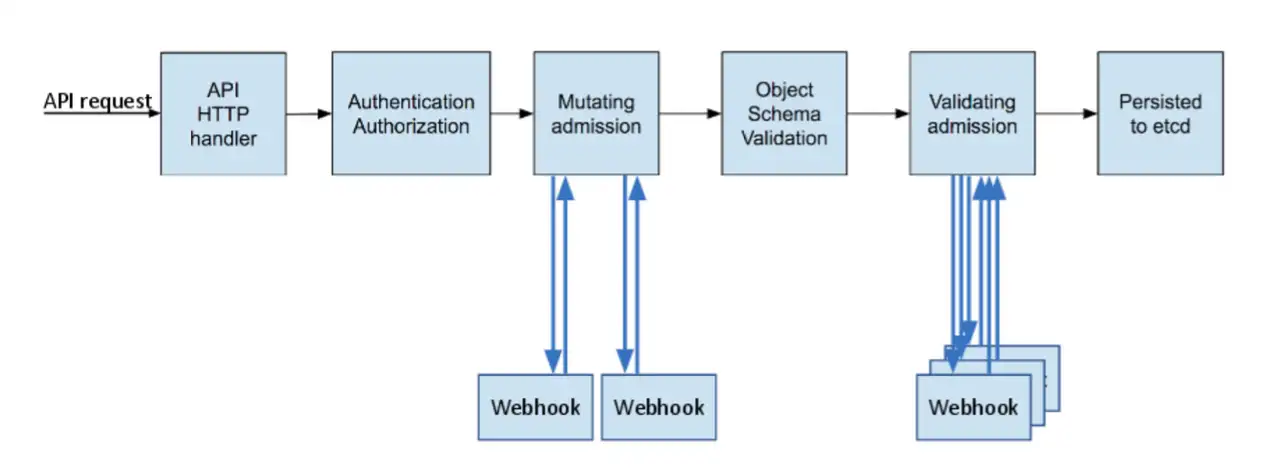
Kubernetes image policy webhook explained
In this article we will explore how webhook works in kubernetes and more specifically about the ImagePolicyWebhook, the kubernetes documentation about it is kind of vague...
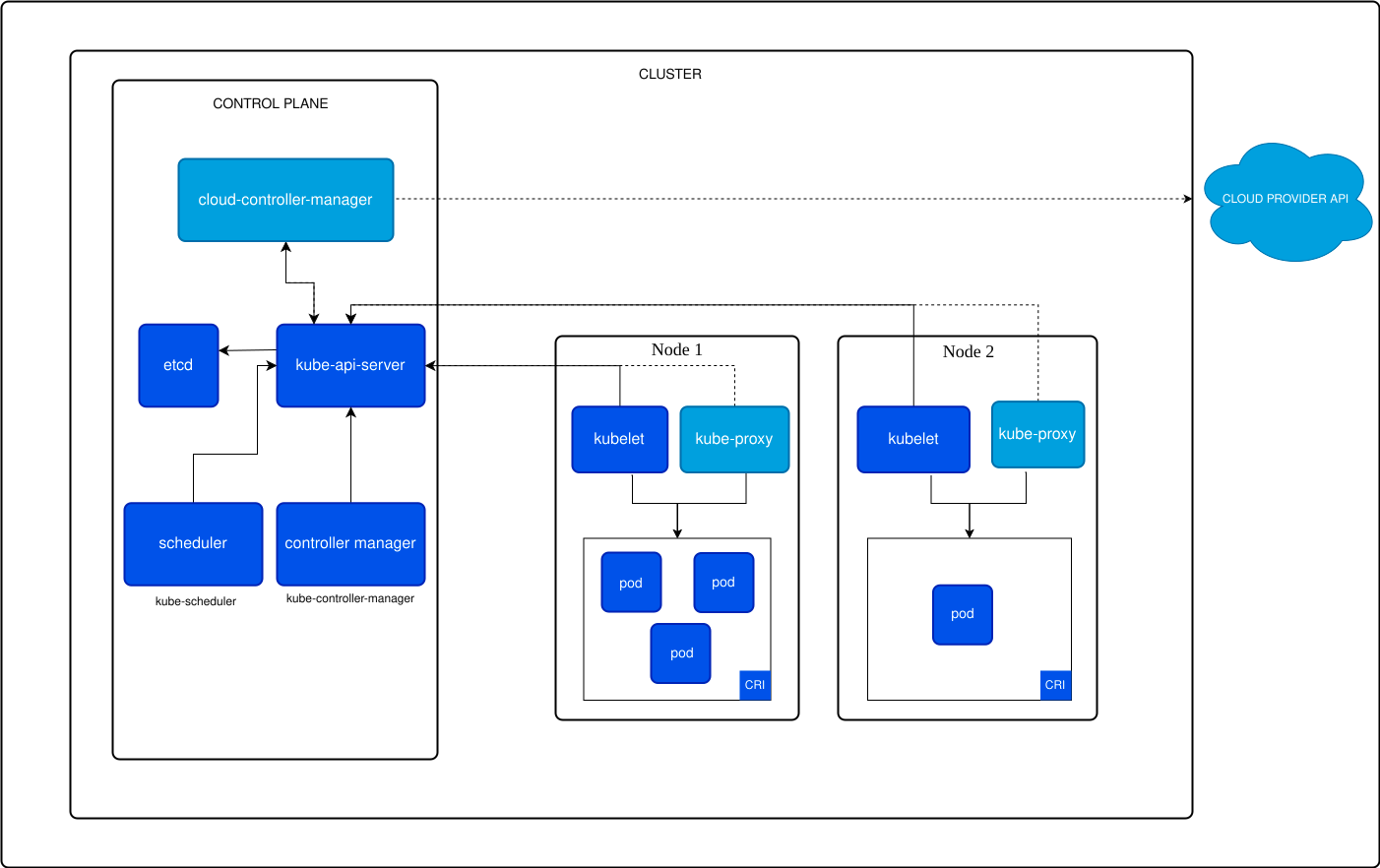
Kubernetes RBAC deep dive: Understanding authorization with kubectl and curl
In this article we will explore how RBAC works in kubernetes at the API level, using both kubectl and raw HTTP calls to understand what's happening under the hood
